On 07, April 2014 a patch was released for OpenSSL to fix a very controversial vulnerablility – The Heartbleed Bug. According to a report, over 500,000 servers were found to be vulnereable but more and more admins are now patching their machines and the numbers are decreasing steadily.
Affected servers are vulnerable to hacking (extraction of information such as user credential’s, cookies, server private keys, Personal Identification Info etc. from the memory). The bug is so big that major websites like Google, Facebook, Tumblr, Instagram, Yahoo, Pinterest etc. were also vulnerable. This exploit is in existence for more than 2 years without anyone’s attention.
In this post you’ll learn to exploit the Heartbleed bug for getting a buggy website’s OpenSSL to spill the contents of its memory and possibly give us the user’s credentials and other information.
Requirement :-
For this tutorial we will be using a great tool i.e. Metasploit Framework. It’s pre-included in Kali Linux.
Steps To Follow :-
First of all, if you’ve haven’t updated your metasploit framework in quit a while i would recommend it doing now, open up a terminal window and type the following command :
set RHOSTS 192.168.1.169
It could take a while for the framework to update. Once the update process is complete we are good to go.
Start the metasploit framework by typing :
Now we will search for the heartbleed exploit using inbuilt search function :
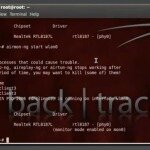
Load up the auxilliary module by typing :
- use auxiliary/scanner/ssl/openssl_heartbleed
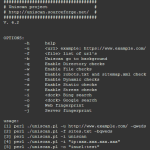
The heartbleed module is now loaded. If you wish to find more information about the module, you may type :
This command reveals the options that we can set in order to use this module and a description of the module.
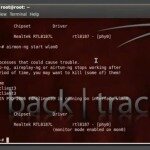
Now we have to set RHOST. RHOST is the ip address of the website which is vulnerable to the exploit.
- set RHOSTS 192.168.1.169
- set verbose true
It’s almost done now, just enter the following command :
If everything went as planned the server will leak about 64K bytes of what was in its memory. This could contain anything from username-password pairs to credit card numbers which is why this hack (along with pretty much all others) is very much illegal to actually try on a live website without the developer’s explicit consent.





I havent had a chance to check this out yet, but usually the “auxiliary/scanner” modules are simply scanners. In this case it would scan for boxes vulnerable to Heart Bleed, not actively exploit it.